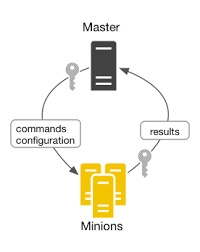
SaltStack, or Salt is a tool which is open source configuration management software and remote execution engine, code deployment and communication topologies. Salt competes with popular cofiguration management tools like chef and puppet. Salt claims to scale up to tens and thousands of servers. Salt has been designed to be highly modular and easily extensible. The design goal is to make Salt easily moldable to diverse applications.
- There is a master server and it connects to the agent servers (called minions) in your infrastructure.
- The master can run commands in the minions parallelly, it is what make salt very fast.
- The minions will execute the command sent by master and return it.
SaltStack installation on centos 7 server.
Login your master server.
Master – 192.168.1.5
To install using the SaltStack repository
rpm --import https://repo.saltstack.com/yum/redhat/7/x86_64/latest/SALTSTACK-GPG-KEY.pub
vi /etc/yum.repos.d/saltstack.repo
[saltstack-repo] name=SaltStack repo for RHEL/CentOS $releasever baseurl=https://repo.saltstack.com/yum/redhat/$releasever/$basearch/latest enabled=1 gpgcheck=1 gpgkey=https://repo.saltstack.com/yum/redhat/$releasever/$basearch/latest/SALTSTACK-GPG-KEY.pub
#yum clean expire-cache
#yum update.
Install the salt-minion, salt-master, or other Salt components:
yum install salt-master yum install salt-minion yum install salt-ssh yum install salt-syndic yum install salt-cloud
#chkconfig salt-master on
#service salt-master start
Configure Master Configuration
Salt configuration is very simple. The default configuration for the master will work for most installations and the only requirement for setting up a minion is to set the location of the master in the minion configuration file.
The configuration files will be installed to /etc/salt and are named after the respective components, /etc/salt/master, and /etc/salt/minion.
By default the Salt master listens on ports 4505 and 4506 on all interfaces (0.0.0.0). To bind Salt to a specific IP, Change the interface conf in /etc/salt/master.
Find:
# The address of the interface to bind to #interface: 0.0.0.0
Replace with:
# The address of the interface to bind to interface: youripaddress
in my case, I have given interface: 192.168.1.5
Setting the states file_roots directory
All of salt’s policies or rather salt “states” need to live somewhere. The file_roots directory is the location on disk for these states. For this article we will place everything into /salt/states/base.
Find:
#file_roots: #base: #- /srv/salt
Replace with:
file_roots: base: - /salt/states/base
Setting the pillar_roots
The last item that we need for now is the pillar_roots dictionary. The pillar system is used to store configuration data that can be restricted to certain nodes. This allows us to customize behavior and to prevent sensitive data from being seen by infrastructure components not associated with the data. This format mirrors the file_roots exactly. The location of our pillar data will be at /srv/pillar:
Find:
#pillar_roots: #base: #- /srv/pillar
Replace:
pillar_roots: base: - /salt/pillars/base
Created those folders.
# mkdir /salt/pillars/base # mkdir /salt/states/base
Restart the salt-master service
# service salt-master restart Redirecting to /bin/systemctl restart salt-master.service
Thats it..
Configure the Salt-Minion Configuration
minion – 192.168.1.6
Install SaltStack repository and update repos as before in /etc/yum.repos.d/saltstack.repo.
Install salt minion
#yum install salt-minion
Update your salt master connection details.
# vi /etc/salt/minion
Find:
#master: salt
Replace with:
master: yourmasterip
in my case, I have given interface: 192.168.1.5
# service salt-minion restart Redirecting to /bin/systemctl restart salt-minion.service
Thats it.. Once the salt-minion service is restarted the minion will start trying to communicate with the master. Go to Master node server and accept the Minions keys.
List the available keys
[root@localhost ~]# salt-key -L Accepted Keys: Denied Keys: Unaccepted Keys: 192.168.1.6 Rejected Keys:
Accept the minion key
[root@localhost ~]# salt-key -a 192.168.1.6 The following keys are going to be accepted: Unaccepted Keys: 209.205.208.100 Proceed? [n/Y] y Key for minion 192.168.1.6 accepted.
To list all the accepted keys
#salt-key --list all
SENDING COMMANDS
Communication between the Master and a Minion may be verified by running the test.ping command:
# salt 192.168.1.6 test.ping
192.168.1.6: True
To list all minion
# salt '*' test.ping 192.168.1.6: True minion2: True minion3: True minion4: True
To check minion disk usage
# salt '192.168.1.6' disk.usage 192.168.1.6: ---------- /: ---------- 1K-blocks: 37329092 available: 36223528 capacity: 3% filesystem: /dev/mapper/centos-root used: 1105564